Hightouch provides out-of-the-box role-based access control (RBAC) to govern what actions a user can take on workspace resources. All accounts come with the default Admin role. Business-tier customers can access the additional default roles and create custom roles as needed.
Users can be only assigned one role. When a user doesn't have sufficient privileges to a resource, the resource is grayed out in the UI.
What is a role?
A role consists of a set of policies defining access to resources in the workspace. A policy is a set of actions, resources, and conditions.
- Actions represent the operations that specific roles can perform, for example,
create,read,update,delete, etc. - Actions are performed on resources—sources, destinations, models, syncs, audiences, account management features, etc.
- (Optional) Conditions determine how policies are applied, for example, you may restrict a policy to resources labeled
project:marketing.
Default roles
All Hightouch workspaces come with the Admin role. These additional predefined roles are available on Business tier plans:
- Admin: This role has unrestricted access to all resources in the workspace. Admins can also manage the workspace itself, including managing user membership and roles, creating new API keys, setting up custom storage, and configuring extensions with external services like Slack and PagerDuty.
- Workspace editor: This role is for advanced business users who need full access to the workspace except for workspace settings, such as user membership and roles. The role has full read and write access to core resources in the workspace. This includes sources, destinations, models, audiences, and syncs. However, the role can't perform any workspace management.
- Model + sync editor: This role is for users, such as business analysts, who regularly manage syncs and modify data. The role has read and write access to models, audiences, and syncs, but can't edit sources and destinations.
- Sync editor: This role is for users, such as growth marketers, who regularly manage syncs, but don't need to modify data. The role has read and write access to syncs (including enabling syncs), but can't edit sources, destinations, and models.
- Audience editor: This role is for users, such as lifecycle marketers, who regularly work with audiences. The role has read and write access to audiences and syncs, but can't edit sources, destinations, models, parent models, and non-audience syncs. It also can't enable syncs or trigger sync runs.
- Source admin: This role is for users, such as data analysts, who need to set up data systems. The role has read and write access to sources and models, but can't edit destinations and syncs.
- Destination admin: This role is for users, such as SaaS administrators, who need to set up downstream business systems. The role has read and write access to destinations, but can't edit sources, models, and syncs.
- Workspace viewer: This role has read-only access to core resources in the workspace. This includes sources, destinations, models, audiences, and syncs. The role can't manage the workspace itself, such as changing workspace configurations.
- Workspace draft contributor: This role is similar to a Workspace editor, except that they can edit sources. However, any edits they make to sources or models require approval before they can go live. Read about approval flows to learn more.
| Source | Model | Dest. | Sync | Audience | Account | |
|---|---|---|---|---|---|---|
| Admin | Full | Full | Full | Full | Full | Full |
| Workspace editor | Full | Full | Full | Full | Full | No Access |
| Model + sync editor | Read | Full | Read | Full | Full | No Access |
| Sync editor | Read | Read | Read | Full | Full | No Access |
| Audience editor | Read | Read | Read | Limited | Full | No Access |
| Source admin | Full | Full | Read | Read | Read | No Access |
| Destination admin | Read | Read | Full | Read | Read | Full |
| Workspace viewer | Read | Read | Read | Read | Read | No Access |
| Workspace draft contributor | Full | Full* | Full | Full* | Full | No Access |
- Full permission indicates that this role can edit resources without approval.
- Full* permission indicates that this role can edit resources but require approval before changes can go live.
- Limited permission indicates that this role has read and write access to view and edit syncs, but it can't enable syncs or trigger sync runs.
Refer to the default role policies for a JSON description of each role.
The Workspace editor and Workspace viewer roles were previously named Editor and Viewer, respectively. You may noticed Editor and Viewer roles in workspaces created before September 2022.
Using roles with approval flows
Approval flows let Business tier customers stage new resources (models and syncs) and changes to existing resources in draft mode until an approver reviews them. Only Workspace Draft Contributors' changes require approval and all roles except Workspace Draft Contributor and Workspace Viewer can grant approval.
If you use approval flows, we recommend using the following roles only:
- Admin - can grant approvals and handle account management
- Workspace editor - can grant approvals
- Workspace draft contributor - can author changes but requires approval
To learn more about how approval flows work, read the approval flows documentation.
Custom roles
For advanced Business tier customers, Hightouch exposes a custom role builder for workspace owners to create their own roles. Custom roles can reference resource labels, and are often used with label-based access control (LBAC).
LBAC combined with custom roles is geared for workspaces with especially sensitive data sets, companies that want finer control of their production syncs, or auditors who want to ensure that SOC2 compliance is maintained.
Customizing roles
To create a custom role in your workspace, go to the Roles tab in the Settings page.
Once there, you can create a new role by clicking on Add Role. You can also edit existing custom roles by clicking on the role name.
In the modal that appears, enter the Name for the custom role.
You can then choose to create role by toggling on the JSON Builder and entering JSON or selecting the role's permissions via checkboxes. If using the UI role builder, don't forget to click Add once you've selected all the role's permissions.
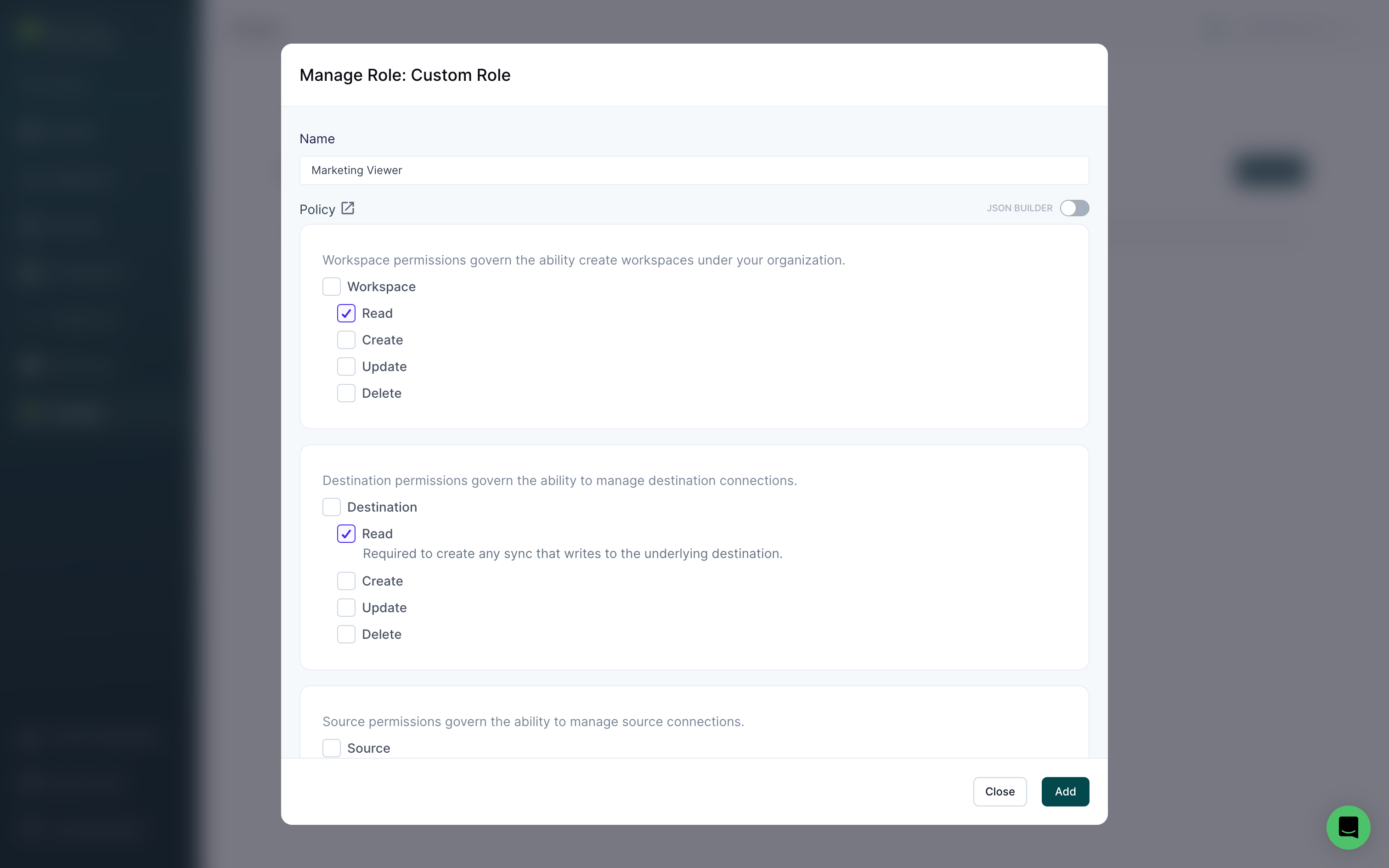
You can only add conditions using the JSON builder, not using the UI role builder.
JSON builder
When using the JSON builder, recall that each role is made of an array of policy objects described in JSON.
Each policy consists of:
- An effect: either
allowordeny - Actions: operations that users assigned to the role are able to complete
- Resources: resources that those actions apply to
- (Optional) Conditions: limitations on when to apply actions
This is an example of a custom role that allows full access to destinations, sources, models, and syncs that have been labeled project:marketing.
Refer to the label-based access control documentation to learn more about how to create roles with conditions.
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": "*",
"resource": [
"destination",
"source",
"model",
"sync"
],
"conditions": {
"labels.project": {
"equals": "marketing"
}
}
}
]
}
By default, all permissions are set to deny. An empty policies array means
that all actions are denied.
Make sure to not edit the "version" date when creating a custom role.
Actions
Actions are operations that users are allowed to make. Hightouch supports permissions on basic CRUD actions for all resources and a set of granular actions for specific resources.
| Action | Description | Applicable Resources |
|---|---|---|
create | Permission to add new resources | All |
read | Permission to view and use existing resources | All |
update | Permission to edit existing resources | All |
delete | Permission to delete existing resources | All |
preview | Permission to view results of a model | Sources and models |
start | Permission to trigger a manual sync | Sync only |
enable | Permission to trigger enable a sync | Sync only |
debugger | Permission to view results of an existing sync | Sync only |
testrow | Permission to test a row in a sync | Sync only |
approve | Permission to approve changes | Syncs and models |
* | Denotes all actions | All |
The read permission on a resource is required when another resource
needs to use it, similar to access permissions in database systems. For
example, for a role to create syncs, the role also needs read permission
on sources and models.
Resources
| Resource | Description | |
|---|---|---|
workspace | Catch-all for workspace-level features like extensions | |
workspace_membership | Permission to invite users | |
source | Access to sources | |
destination | Access to destinations | |
model | Access to models | |
sync | Access to syncs | |
alert | Access to alerts on syncs | |
audience | Access to individual audiences | |
audience_schema | Access to audience setup, including parent models, event models, and related models | |
sync_templates | Access to sync templates |
Default role policies
Admin
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": "*",
"resource": "*"
}
]
}
Workspace editor
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": "*",
"resource": [
"destination",
"source",
"model",
"sync",
"audience",
"audience_schema",
"sync_template",
"workspace_membership",
"alert"
]
}
]
}
Model and sync editor
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": [
"read",
"preview"
],
"resource": [
"source",
"destination"
]
},
{
"effect": "allow",
"actions": "*",
"resource": [
"model",
"sync",
"audience",
"audience_schema",
"sync_template",
"alert"
]
}
]
}
Sync editor
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": "read",
"resource": [
"source",
"destination",
"model"
]
},
{
"effect": "allow",
"actions": "*",
"resource": [
"sync",
"audience",
"audience_schema",
"sync_template",
"alert"
]
}
]
}
Audience editor
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": "read",
"resource": [
"source",
"destination",
"model",
"audience_schema",
"sync_template",
"alert"
]
},
{
"effect": "allow",
"actions": [
"create",
"read",
"update"
],
"resource": [
"sync"
]
},
{
"effect": "allow",
"actions": "*",
"resource": [
"audience"
]
}
]
}
Source admin
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": "*",
"resource": [
"source",
"model"
]
},
{
"effect": "allow",
"actions": "read",
"resource": [
"destination",
"sync",
"sync_template",
"audience",
"workspace_membership",
"workspace"
]
}
]
}
Destination admin
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": "read",
"resource": [
"source",
"model"
]
},
{
"effect": "allow",
"actions": "*",
"resource": [
"destination",
"sync",
"audience",
"audience_schema",
"sync_template",
"alert",
"workspace_membership",
"workspace"
]
}
]
}
Workspace viewer
{
"version": "2022-04-26",
"policies": [
{
"effect": "allow",
"actions": [
"read"
],
"resource": [
"source",
"destination",
"model",
"sync",
"audience",
"audience_schema",
"sync_template",
"workspace_membership",
"alert"
]
}
]
}